NTLM Security Support Provider
NTLMSSP is a Microsoft protocol for authentication using the NTLM protocol.
Open specification: [MS-NLMP]
Decryption of NTLM-encrypted traffic
Wireshark knows how to decrypt NTLM-encrypted traffic, as long as you give it the required secrets. Then it can decrypt the NTLM exchanges: both the NTLM challenge/response and further protocol payloads (like DCE/RPC that may be encrypted with keys derived from the NTLM authentication.
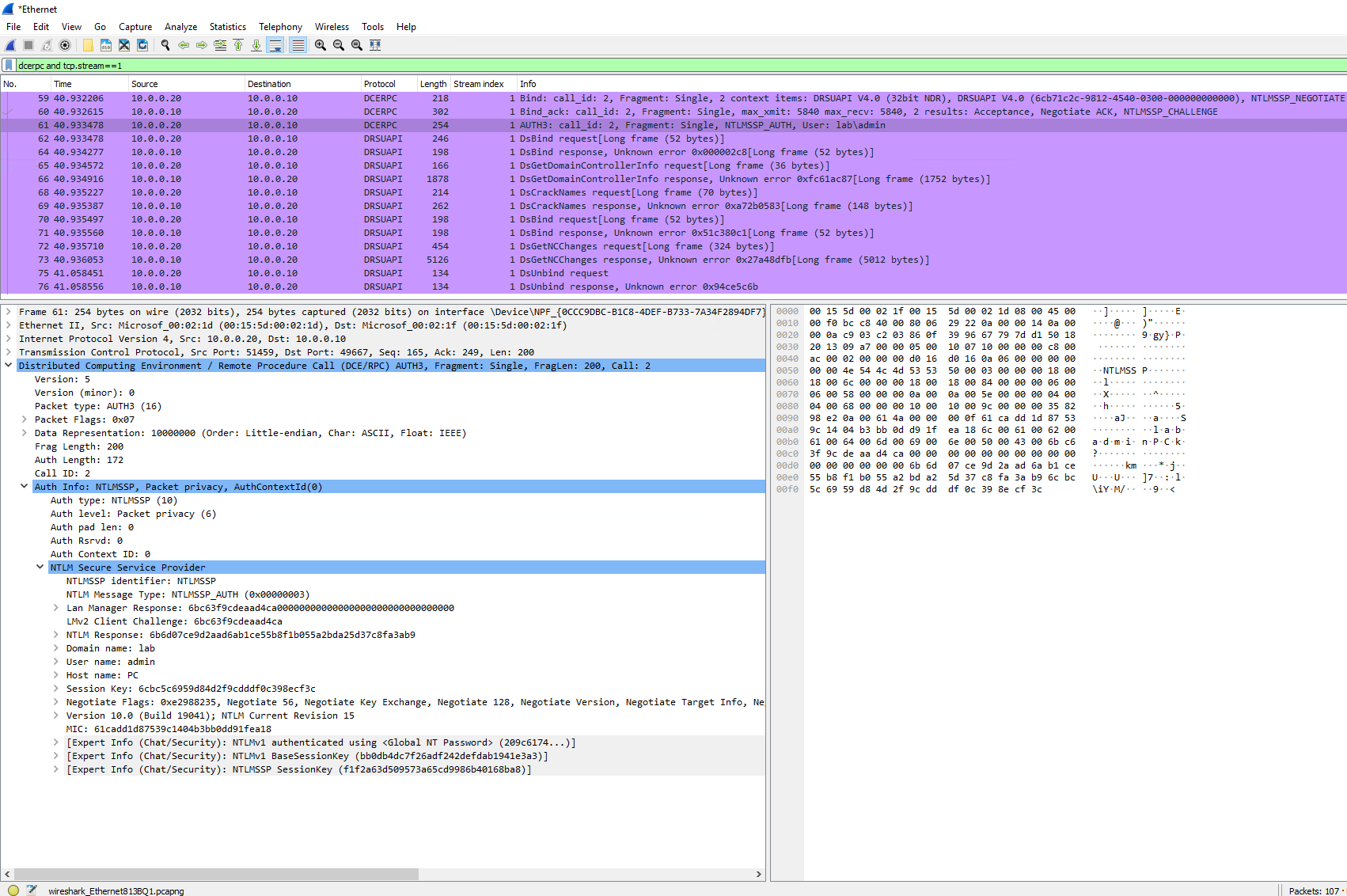
Here's how the NTLM authentication at the beginning of a DRSUAPI (DCE/RPC) session looks like before providing the password or the hash:
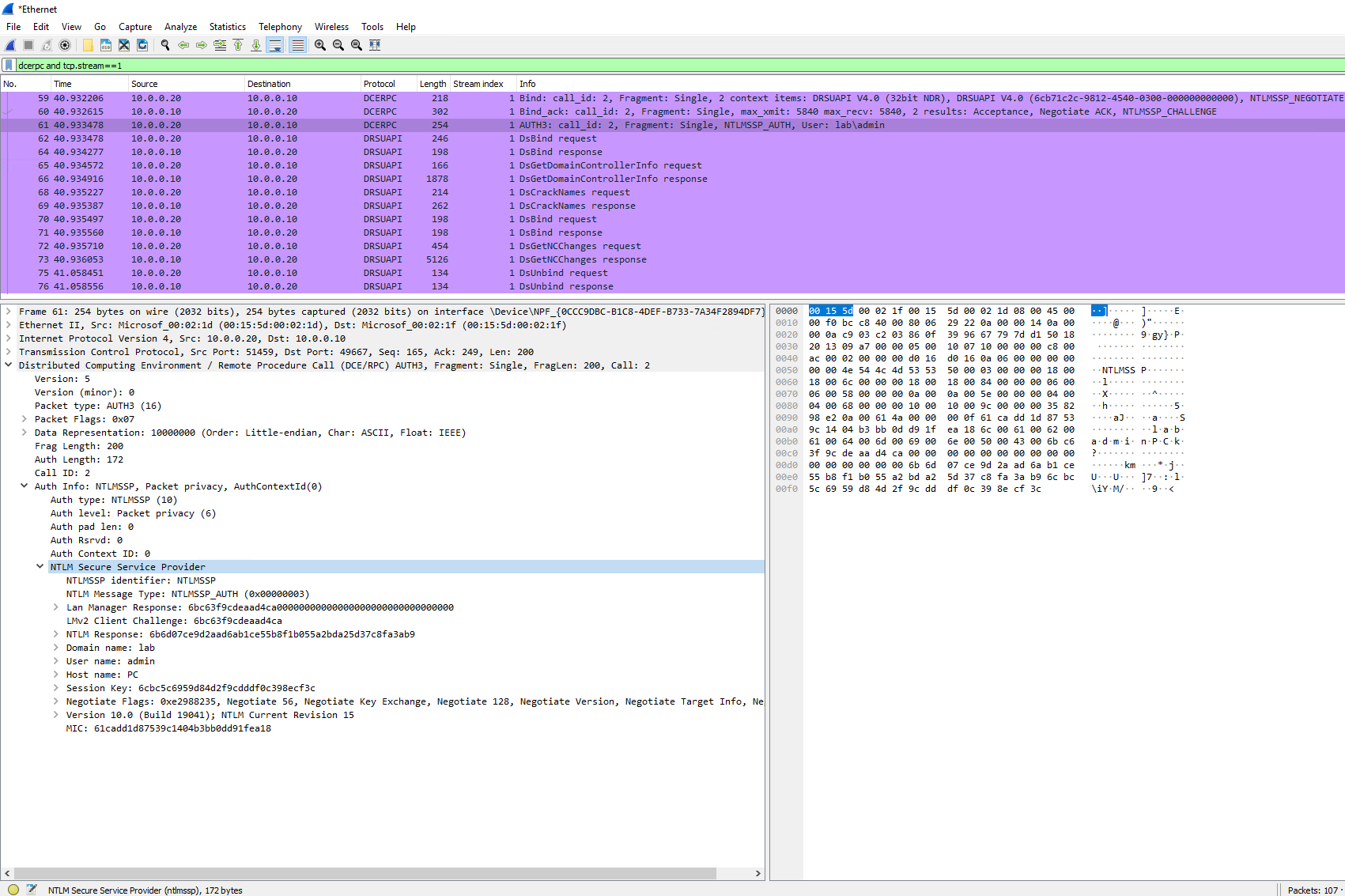 And after providing the password/hash, notice the additional info highlighted in blue:
And after providing the password/hash, notice the additional info highlighted in blue:
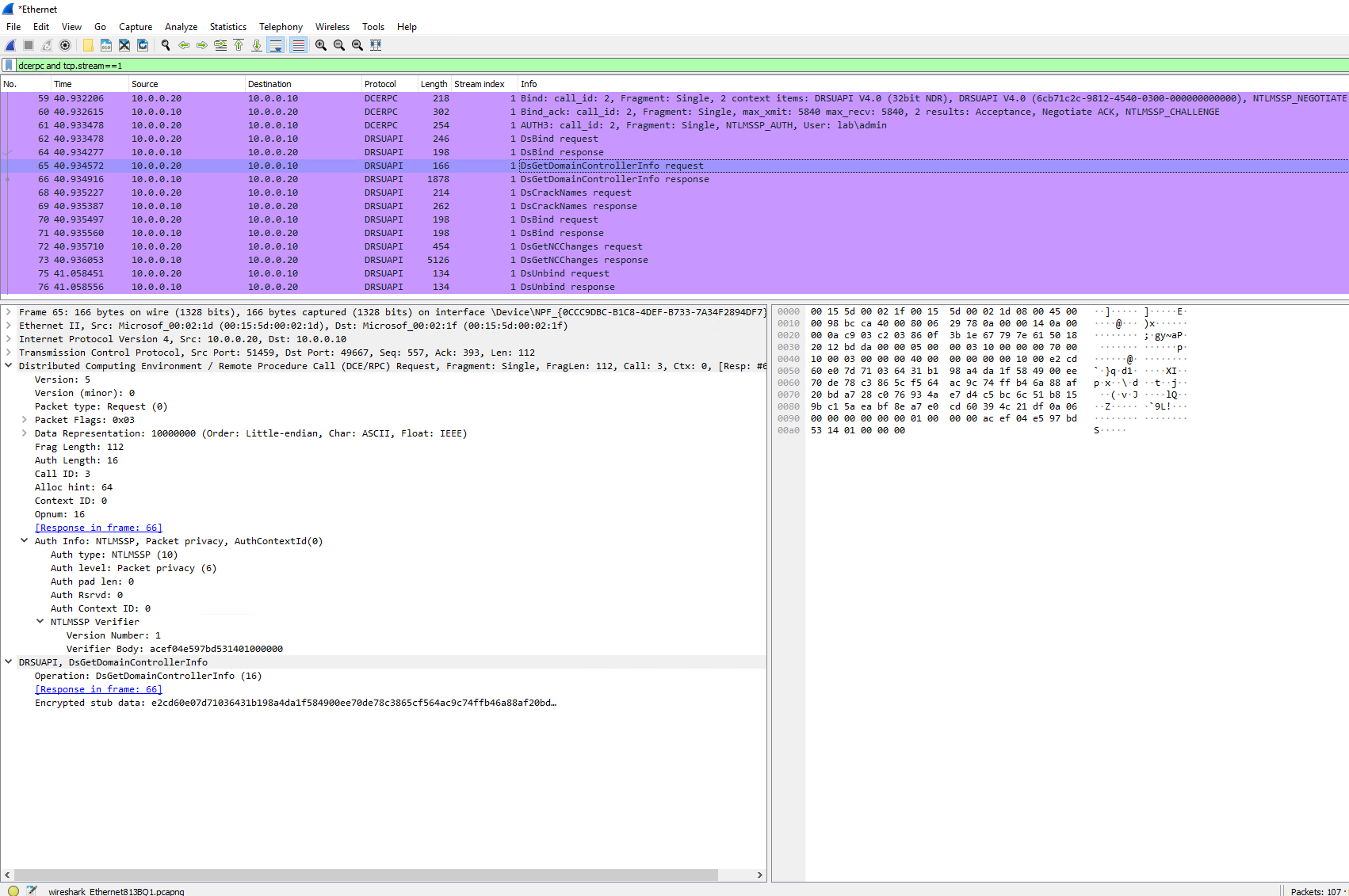
Then, before providing the password/hash, the DsGetDomainControllerInfo request payload is not readable since it's "encrypted stub data":
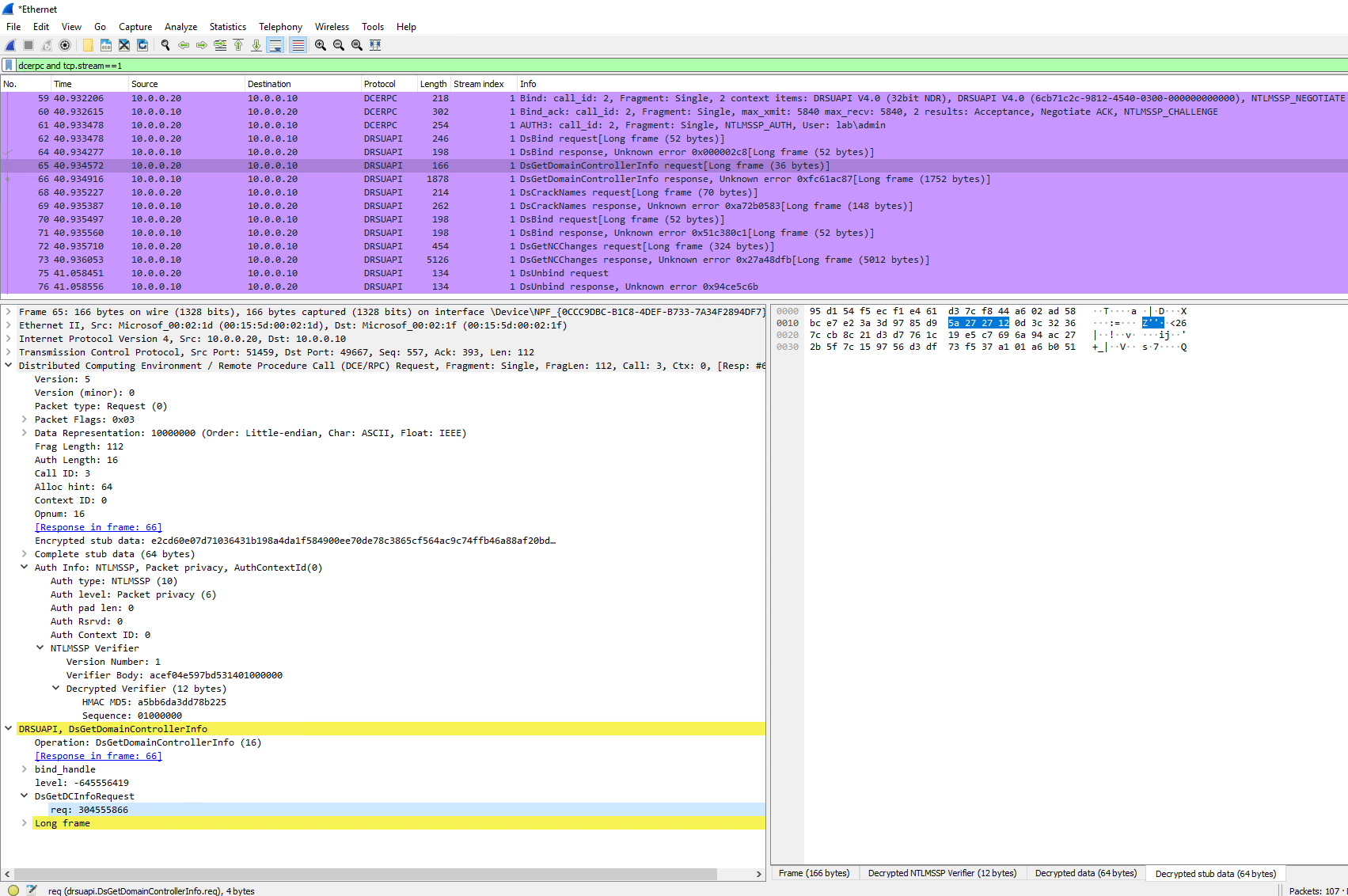
But after providing the password/hash, it becomes "decrypted stub data" (decrypted data is invalid in this screenshot due to bug #19000 (closed) which was fixed in v4.0.6, backported to v3.6.14)
By providing the NT hash in a keytab file
If you only have the NT hash (aka "NTLM hash" ) of the account, you can still decrypt NTLM encrypted traffic by providing the hash in a keytab file (yes it's surprising since a keytab file is usually meant for Kerberos, but it works!). You can refer to this Decrypt Kerberos/NTLM “encrypted stub data” in Wireshark tutorial which describes how to create the keytab file and to pass it to Wireshark. This technique is also explained in this Capture-the-Flag challenge write-up: Insomni'Hack Teaser 2023 - Autopsy
By providing the plaintext password in the "NT Password" setting
The "NT Password" setting can contain a password. Go to Edit -> Preferences -> Protocols -> NTLMSSP. Just input the user's password in the "NT Password" field.
According to the source-code, only ASCII passwords are supported (due to the simple method for Unicode encoding). If you only have the NTLM hash: see above.