Remote Execution Protocol (exec)
The exec protocol (sometimes known as rexec) is used to run a program on a remote server as if it was being run on the local machine. This is acomplished by redirecting standard in/out and standard error through the connection. The server running exec receives a connection from a client by opening a socket. The server waits for four null terminated strings (that may come in 2, 3 or 4 packets):
- Standard error stream port
- Username
- Password
- Command to run on server
After these strings have been received, control is passed to the program specified in the command to run on server string.
History
The exec protocol was first added to 4.2BSD and was later determined to be insecure. The main security issue for the protocol is that it does not encrypt data, which allows usernames and passwords to be viewed with a packet sniffer.
Protocol dependencies
- TCP: The exec protocol is typically run over TCP port 512, as assigned by the IANA.
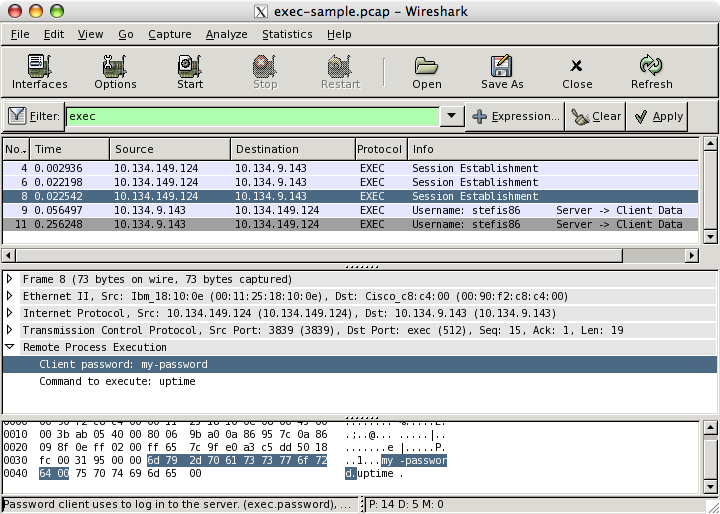
Example traffic
Wireshark
The exec dissector is fully functional. In some instances, such as when packets are lost, the state of the connection cannot be tracked properly. If the state is lost, the fields may show in the wrong order (for example, the password showing up as the username field).
Preference Settings
The exec protocol has two preference settings in Wireshark:
-
Show username in info column? Controls the display of the session's username in the info column. This is only displayed if the packet containing it was seen during this capture session.
-
Show command in info column? Controls the display of the command being run on the server by this session in the info column. This is only displayed if the packet containing it was seen during this capture session.
Example capture file
Display Filter
A complete list of exec display filter fields can be found in the display filter reference
Show only the exec traffic:
execCapture Filter
You cannot directly filter the exec protocol while capturing. However, if you know the TCP port used (see above), you can filter on that one.
Capture only the exec traffic over the default port (512):
tcp port 512External links
Discussion
Imported from https://wiki.wireshark.org/Exec on 2020-08-11 23:13:56 UTC